The OSI Model Explained: How It Works in Networking
Exploring the OSI Model and Its Network Protocols in Detail
In our modern world, where effective communication is vital to daily life, data transfer over the internet has become essential.
Yet, have you paused to consider how this intricate procedure operates with such ease?
At its core, a powerful framework known as the OSI (Open Systems Interconnection) model oversees this intricate data transfer. The OSI model is the unsung hero that facilitates the internet we depend on, ensuring that information travels reliably, securely, and efficiently across networks.
Greetings, everyone! My name is Ikbal. In this blog entry, I will delve into the essential principles of the OSI (Open Systems Interconnection) model, outlining its seven layers along with the relevant protocols, and explaining how it enables smooth data transmission over the Internet.
What is the OSI Model? An Insight Into Its Layers and Functions.
The OSI (Open Systems Interconnection) model is made up of seven layers that promote effective data transfer between networks. It includes a collection of standardized protocols that outline how various computer systems interact over a network. These seven layers are essential for the functioning of the modern internet.
Layers of the OSI Model
The OSI Model consists of 7 layers, and each layer has a distinct function in managing data. All the layers are listed below:
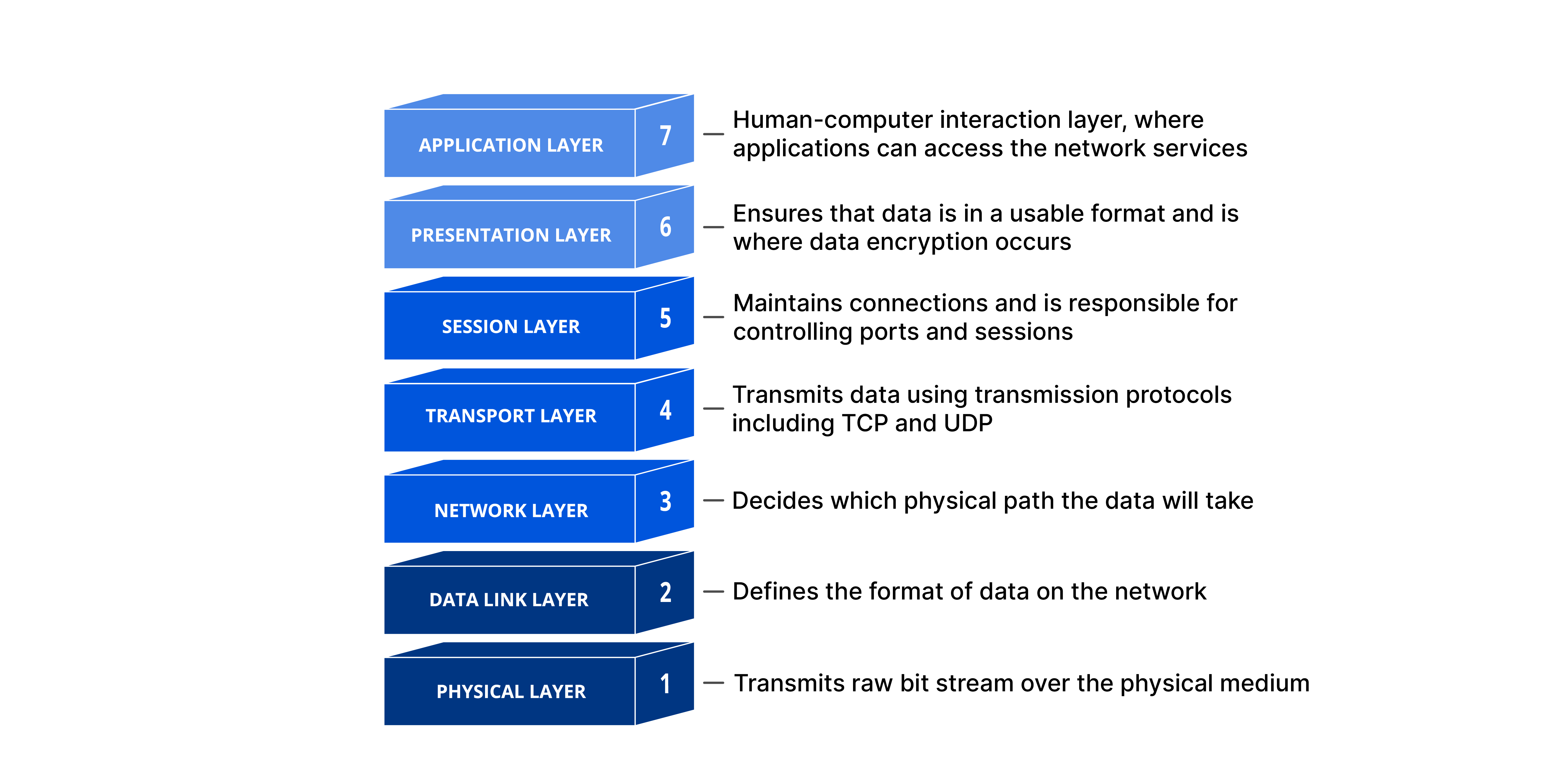
We will go through the layers of the OSI model using a top-down method, beginning with the Application Layer and progressing down to the Physical Layer.
Application Layer
At the top of the OSI model lies the Application Layer. This layer generates the data that needs to be transmitted over the network. This layer additionally functions as a portal for the application service to connect to the network and for presenting the received information to the user.
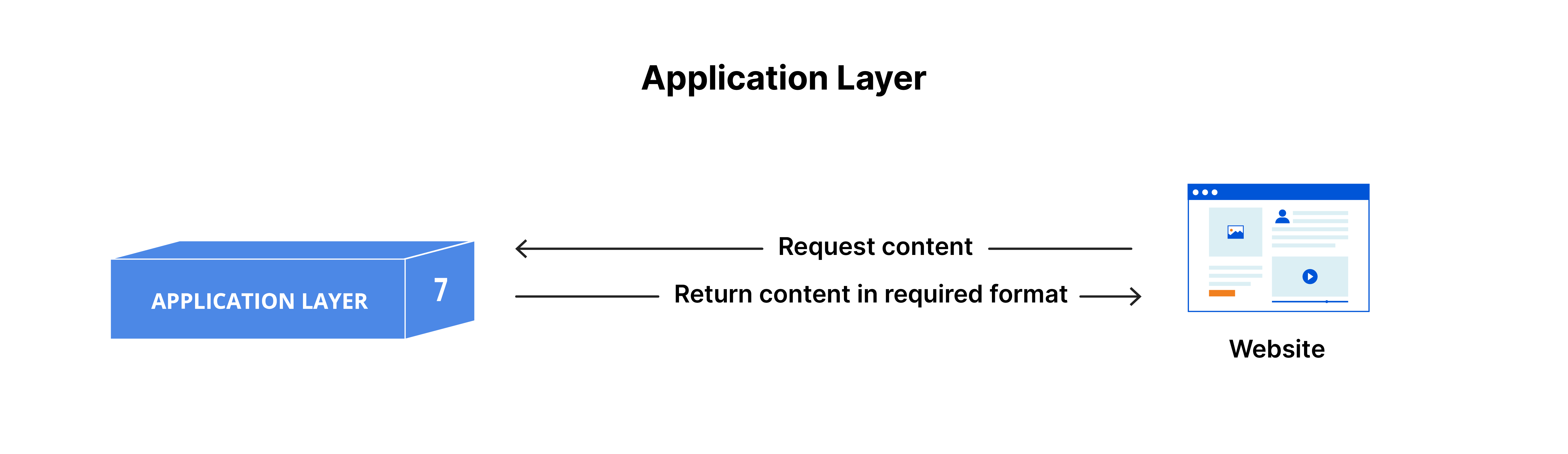
Aplication Layer Protocols
Application layer protocols establish guidelines and provide services that allow applications to communicate over a network, as well as dictate how applications share data in an organized manner.
Application Layer protocols consist of:HTTP (HyperText Transfer Protocol): Utilized for the transmission of web pages and data across the internet.
FTP (File Transfer Protocol): Employed for transferring files between computers within a network.
SMTP (Simple Mail Transfer Protocol): Employed for the dispatch and receipt of emails.
DNS (Domain Name System): Converts domain names (such as www.example.com) into IP addresses.
Presentation Layer
The presentation layer is responsible for formatting the data so that it can be understood by the application layer. This layer manages functions such as data encoding, encryption, and compression, which are essential for the secure and efficient transmission of data over the network.
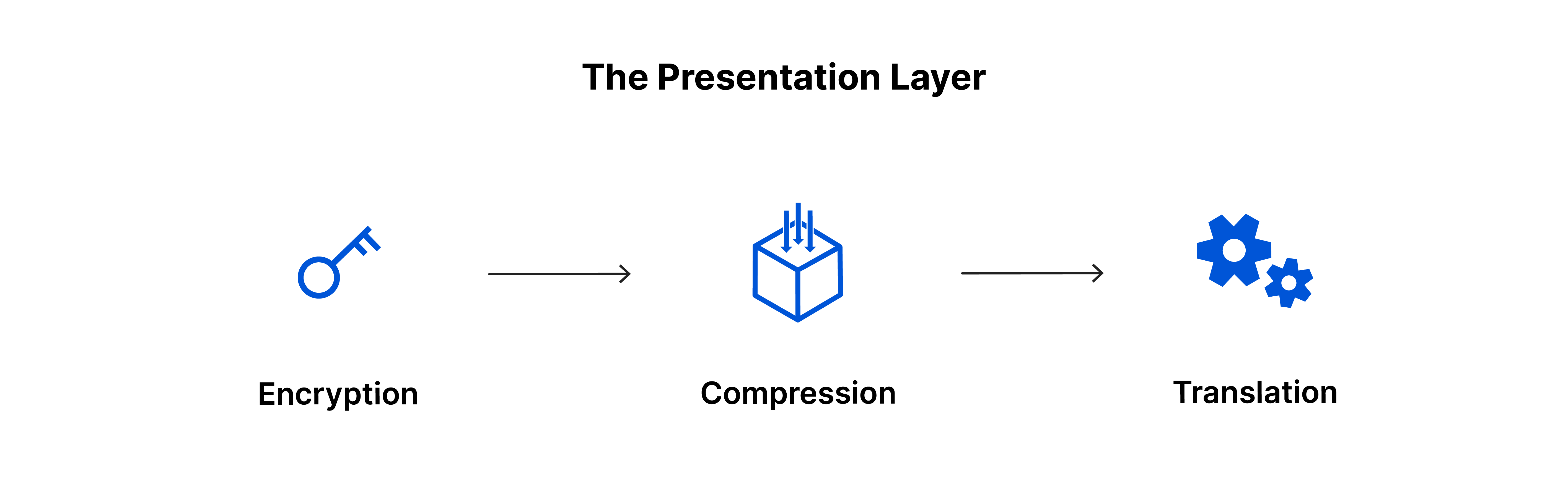
Key Functions of the Presentation Layer:
Data Translation (Encoding/Decoding):
This layer guarantees that the data is appropriately formatted for the system receiving it. It manages the data encoding procedure, transforming the data into a format that both the sender and receiver can understand.Encryption:
The Process of transforms data into an encrypted format before transmission and reverses the process upon receipt, safeguarding privacy and security during communication.
For instance, web interactions are protected using SSL/TLS encryption protocols.Compression:
This process decreases the amount of data transmitted across the network, resulting in quicker and more effective transmission.
Instances of this include ZIP file compression and JPEG image compression.
Session Layer
This layer is tasked with setting up, overseeing, and ending communication sessions between two devices. It guarantees that the data exchange between the two devices happens in an organized and synchronized way.

Key Responsibilities of the Session Layer
Connection Establishment and Termination:
The Session Layer manages the establishment and termination of communication sessions. It sets up the link between devices, oversees the data exchange process, and ensures that the session is properly closed once the communication has finished.Synchronization:
This layer guarantees that data remains synchronized across devices while communicating. It can handle checkpoints, which facilitate the resumption of data transmission in the event of an interruption or failure.
Transport Layer
The Transport Layer serves as a link between the Application Layer and the Network Layer. It collects data from the Application Layer, breaks it into segments, and sends it to the Network Layer for delivery. After that, it accepts data from the Network Layer, reconstructs it, and forwards it to the Application Layer.
Segments: In the Transport Layer, the data is called segments.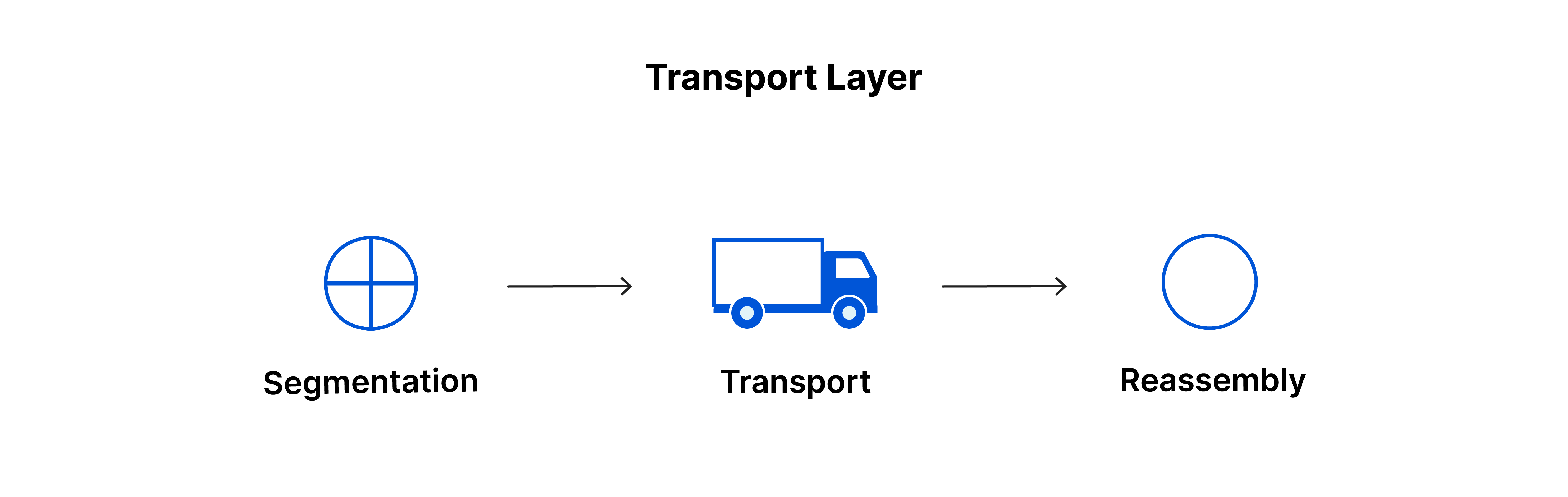
Key Responsibilities of the Session Layer
Segmentation:
The information obtained from the Application Layer is divided into smaller units referred to as segments.
Reliable Data Transmission:
The Transport Layer guarantees data delivery by employing acknowledgements (ACKs) to validate successful transmission.- If any issues are identified, it will resend the data to ensure it arrives at its intended destination accurately.
Protocol Usage:
The Transport Layer utilizes two primary protocols:TCP (Transmission Control Protocol): Guarantees dependable data transmission through acknowledgments (ACKs) and error detection.
UDP (User Datagram Protocol): Designed for quicker, less reliable communication where speed takes precedence over reliability (for example, video streaming).
Data Flow Between Layers:
Sender Side:
The Transport Layer gets data from the Application Layer, divides it into segments, and sends it to the Network Layer for sending across the network.
Receiver Side:
On the receiving side, the Transport Layer takes data from the Network Layer, reconstructs the segments, and then forwards the data to the Application Layer.
Port Number Management and Application-Specific Routing
It includes source and destination port numbers in its header to guarantee that the data reaches the correct application on the receiving device.
On the recipient side, the Transport Layer guarantees that incoming data is accurately sent to the appropriate application according to the port number.
Every application operating on the device utilizes a designated port for communication, enabling the Transport Layer to direct the data to the correct application.
Network Layer
The Network Layer plays a critical role in transmitting data across different networks. It guarantees that data is efficiently directed from the source device to the destination device, while handling important functions such as routing, addressing, and packet forwarding.
Key Responsibilities of the Network Layer:
Packetization:
The Network Layer breaks data down into smaller pieces known as packets to facilitate efficient transmission.Routing and Path Determination:
The Network Layer identifies the optimal path for data to travel through various available routes.
It chooses the most efficient route considering elements such as network structure, traffic conditions, and routing protocols.Logical Addressing:(IP Addressing)
To facilitate efficient communication within a network, the Network Layer allocates a distinct address to every device. This address plays a crucial role in uniquely identifying devices within the internetwork.IP (Internet Protocol):
The main protocol utilized for addressing and routing packets in the network layer is the Internet Protocol (IP).
IPv4 (Internet Protocol Version 4):
Uses a 32-bit address structure.
Example: 192.168.1.1.IPv6 (Internet Protocol Version 6):
Uses a 128-bit address structure.
Example: 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
Data Link Layer
It guarantees reliable interaction between nodes that are directly linked or facilitates data transmission between two devices within the same network by managing error detection, flow regulation, and framing.
Key Responsibilities of the Data Link Layer
Framing:
The Data Link Layer arranges the raw bits received from the Physical Layer into frames.Frame: it refers to the envelope in which the packets are packaged and sent to the recipient.
Analogy: The Journey of Data – From Package to Delivery
Imagine you want to send a present to a friend who lives nearby. Here is the parcel(Packet) containing both the recipient's and sender's addresses (IP addresses).
To deliver the parcel, you use a truck (frame). The truck knows your friend’s precise location in the neighborhood (MAC address).
The frame operates similarly to the truck, ensuring that the parcel reaches the right destination within the local network.
In this way, the data link layer makes sure that the truck (frame) transports the parcel (Packet) to the correct address (MAC address) within the appropriate area (local network).
What is MAC Address?
A MAC address (Media Access Control address) is a distinct identifier assigned to a device's NIC (network interface card) that enables it to connect to a network.
Physical Layer
The Physical Layer, which is the bottom layer of the OSI model, handles the transmission of raw binary data (bits) between nodes through a physical medium, like Ethernet cables or radio frequencies (for instance, Wi-Fi).
How Data Flows Through the OSI Model
For human-readable data to be transmitted over a network from one device to another, the information needs to pass through the seven layers of the OSI Model on the sending device and subsequently ascend through the same seven layers on the receiving device.
For instance, Mr. Ikbal intends to send an email to Ms. Debasmita. After composing the message, he clicks 'send.'
The email application will transmit the message to the application layer, which will select the SMTP protocol before passing the data to the presentation layer. Next, the presentation layer will compress the information before it reaches the session layer, which will initiate the communication session.
Subsequently, the data will enter the sender's transport layer, where it will be segmented. Then these segments will be transformed into packets at the network layer, which will further divide them into frames at the data link layer. Finally, the data link layer will transmit those frames to the physical layer, which will convert the data into a stream of binary digits (1s and 0s) and send it through a physical medium, such as a cable.
After Ms. Debasmita’s computer obtains the bit stream via a physical medium like her wifi, the information will travel through the same sequence of layers on her device, but in reverse order.
Conclusion
In this piece, I've discussed how comprehending the OSI model has greatly improved my understanding of data transmission across networks. Each level serves its unique function, ranging from guaranteeing dependable data delivery to efficiently managing addressing and routing. By studying the protocols and mechanisms at each stage, I now possess a more precise understanding of the intricacies involved in Internet communication. Keep an eye out for further insights as we delve deeper into networking principles and technologies.
